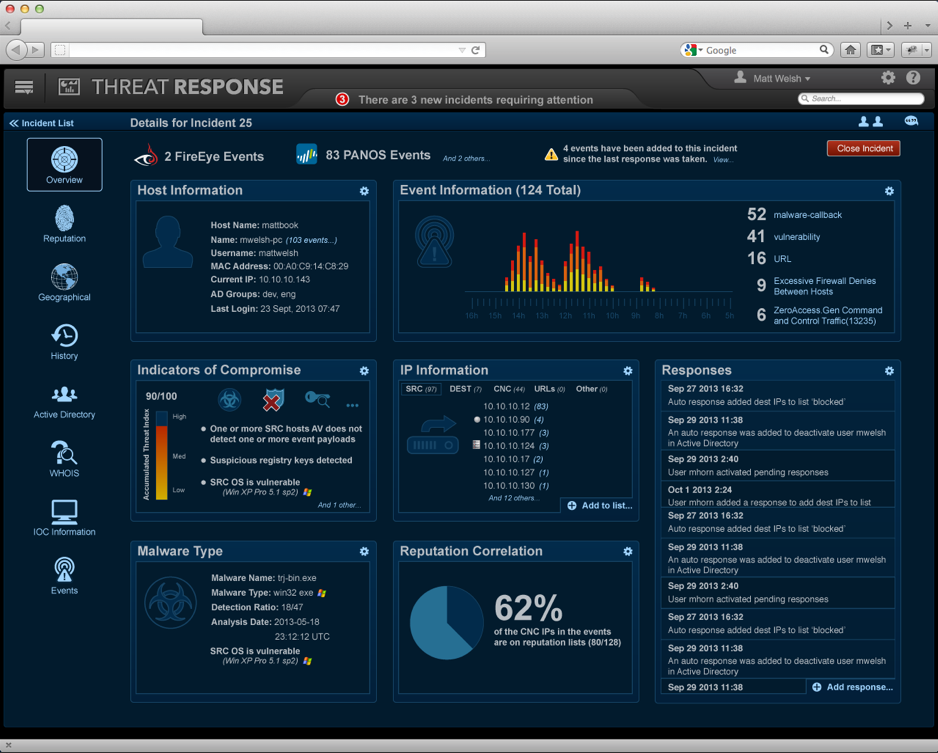
Roles & Responsibility
I was hired into Netcitadel as employee number one, and was the sole designer for both One Control and Threat Control (later called Threat Response).
Since it was a greenfield project I was able to run a solid end-to-end UCD process. This meant understanding who are users are, quick ideation using
white boarding, low fidelity paper sketches (for "design walls"), card sorting exercises to determine the optimal IA, high fidelity clickable mockups,
and finally pixel perfect interactive redlines.
It was also my responsibility to test designs with users, summarize results of those tests, and adjust designs to include feedback, while making sure that
the implementation reflected the design accurately.